Station Farm
iSaacutive Full Factory Program for 3IG
The architecture of the iSaac system is designed to be scalable. The Station Farm means: unlimited. You get unlimited.
Site by Site
Any iSaac Check EndPoint / interface
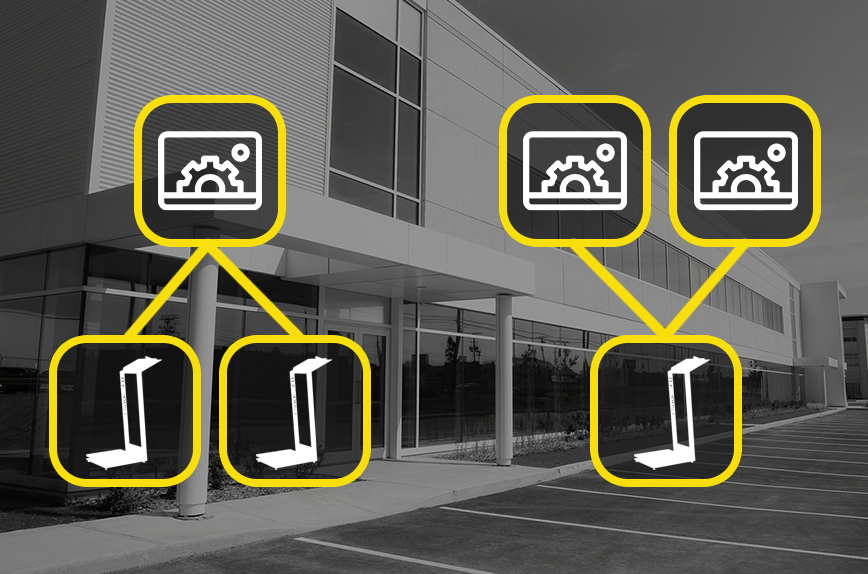
The effectiveness of supervision within a site, security system unit is a direct consequence of the definition of the legal and professional check points established by the delimiting "concentric" security zones. We recommend system technology to opitimize immunity, risk management ability. With iSaac any number of check points can be created, wich can be monitored from one location, or if you need the reverse, the information of a check point can be forwarded to an unlimited number of locations. The operational characteristics dictate, You decide: one operator - countless check points or one check point - countless operators. The information can not be lost, it is only tranferred. Sharing knowledge is the sustainable security.
Any iSaac Area / sub system
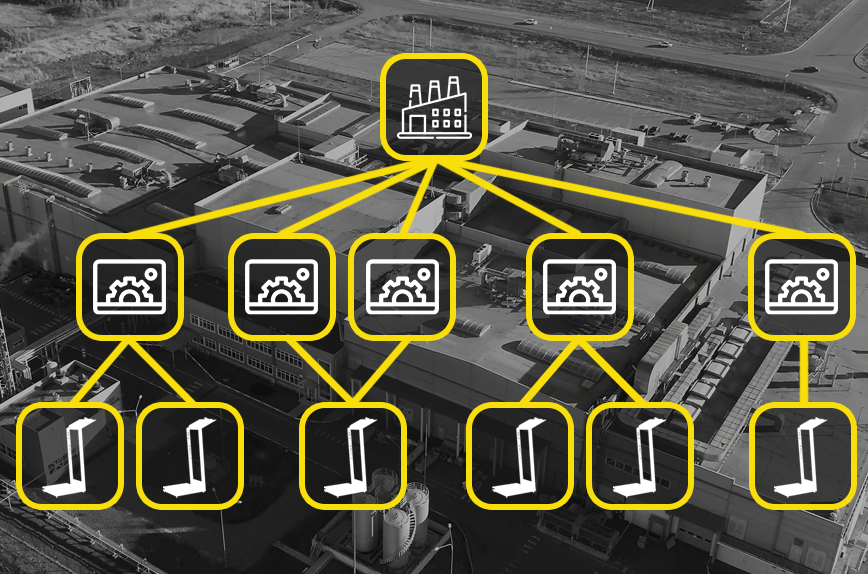
The safety of the site security is greatly influenced by the effectiveness of the check points assigned to the space changes and the flow paths across the zones. In these check points as many RPA robots are needed as the passage requires. When calibrating, the number of passing traffic and their status, the espected passage speed, the available time window and the nominal performance of the RPA robots must be taken into account. With professional infrastructure development, we idealize the desired traffic dynamic and achieve 100 % control. Real security data from the front line, even from every point of entry. We audited the risk information in the entire zone structure.
Any iSaac Factory / main system
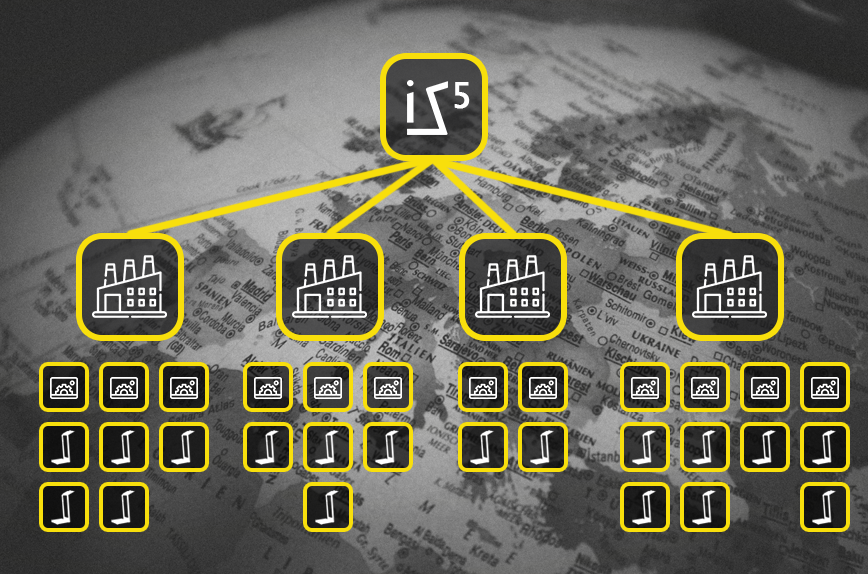
When we want to specify and algorithmize the security system center, we must have typed, controlled, aggregated measurement data from the system units, from the real environment, so we can diversify the operation in a corporate level in the most effective way. The iSaac Site by Site Security System (iS5) is the necessary security infrastructure to automate the security information flow, so the top risks are known. The iSaac Corporate level main system is made up of sites, which are fed with measurement data by the stations and station farms operating in the area. This is the ecosystem of security risk management and security management development.

